How Russia’s operatives flooded Facebook and Twitter with fake & robot accounts to help Donald Trump & attack Hillary Clinton in 2016 Presidential campaign
Scott Shane writes for The New York Times:
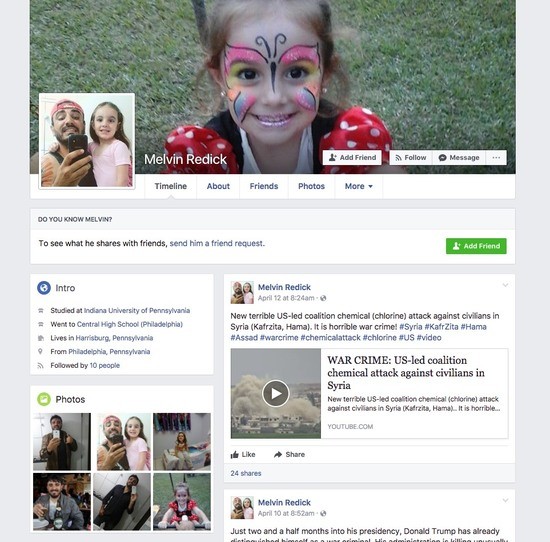
Sometimes an international offensive begins with a few shots that draw little notice. So it was last year when Melvin Redick of Harrisburg, Pa., a friendly-looking American with a backward baseball cap and a young daughter, posted on Facebook a link to a brand-new website.
“These guys show hidden truth about Hillary Clinton, George Soros and other leaders of the US,” he wrote on June 8, 2016. “Visit #DCLeaks website. It’s really interesting!”
Mr. Redick turned out to be a remarkably elusive character. No Melvin Redick appears in Pennsylvania records, and his photos seem to be borrowed from an unsuspecting Brazilian. But this fictional concoction has earned a small spot in history: The Redick posts that morning were among the first public signs of an unprecedented foreign intervention in American democracy.
The DCLeaks site had gone live a few days earlier, posting the first samples of material, stolen from prominent Americans by Russian hackers, that would reverberate through the presidential election campaign and into the Trump presidency. The site’s phony promoters were in the vanguard of a cyberarmy of counterfeit Facebook and Twitter accounts, a legion of Russian-controlled impostors whose operations are still being unraveled.
The Russian information attack on the election did not stop with the hacking and leaking of Democratic emails or the fire hose of stories, true, false and in between, that battered Mrs. Clinton on Russian outlets like RT and Sputnik. Far less splashy, and far more difficult to trace, was Russia’s experimentation on Facebook and Twitter, the American companies that essentially invented the tools of social media and, in this case, did not stop them from being turned into engines of deception and propaganda.
An investigation by The New York Times, and new research from the cybersecurity firm FireEye, reveals some of the mechanisms by which suspected Russian operators used Twitter and Facebook to spread anti-Clinton messages and promote the hacked material they had leaked. On Wednesday, Facebook officials disclosed that they had shut down several hundred accounts that they believe were created by a Russian company linked to the Kremlin and used to buy $100,000 in ads pushing divisive issues during and after the American election campaign.
On Twitter, as on Facebook, Russian fingerprints are on hundreds or thousands of fake accounts that regularly posted anti-Clinton messages. Many were automated Twitter accounts, called bots, that sometimes fired off identical messages seconds apart — and in the exact alphabetical order of their made-up names, according to the FireEye researchers. On Election Day, for instance, they found that one group of Twitter bots sent out the hashtag #WarAgainstDemocrats more than 1,700 times.
The Russian efforts were sometimes crude or off-key, with a trial-and-error feel, and many of the suspect posts were not widely shared. The fakery may have added only modestly to the din of genuine American voices in the pre-election melee, but it helped fuel a fire of anger and suspicion in a polarized country.
Given the powerful role of social media in political contests, understanding the Russian efforts will be crucial in preventing or blunting similar, or more sophisticated, attacks in the 2018 congressional races and the 2020 presidential election. Multiple government agencies have investigated the Russian attack, though it remains unclear whether any agency is focused specifically on tracking foreign intervention in social media. Both Facebook and Twitter say they are studying the 2016 experience and how to defend against such meddling.